Secret Double Octopus – Shared User Accounts

Secret Double Octopus
In our previous blog post titled Passwordless Authentication for Domain-Joined Machines, we dove into the end-user experience and the authentication flow process for the Octopus Authenticator. In this post, we are going to expand upon this concept and dig into how Secret Double Octopus provides secure, passwordless multi-factor authentication for shared user accounts. As a quick recap, the Secret Double Octopus passwordless authentication platform is a highly scalable, reliable and easy to use system designed to help organizations large and small increase their security and improve their end user experience. Direct Business Technologies is a strategic partner and integrator of the Secret Double Octopus platform. You can find additional details about our passwordless authentication services here.
The Secret Double Octopus platform eliminates the need for users to enter in passwords across the enterprise. Secret Double Octopus provides many integration capabilities for organizations to integrate applications and authentication flows into the passwordless authentication process.
Shared User Accounts – Typical Use Cases
It is a best practice to not use shared user accounts, however, in many organizations it is simply not possible to have dedicated users for all systems and workflows. Secret Double Octopus provides a mechanism to perform Passwordless Authentication using shared user objects while still securing the authentication process and providing a full audit trail of what user logged into a shared user object, on what machine and at what time. This auditing is critical for compliance requirements.
Use Case 1 – Domain Administrator
Best practices would be to not have any user objects within your Domain Admins group, as detailed here, however, that is not always practical or possible. The majority of organizations we work with do not have their domain admins group empty and have at least one domain admin. For organizations that require shared domain admins in an auditable and passwordless fashion, Secret Double Octopus is the answer.
Another common scenario we see with shared domain admins is from Managed Services Providers (MSPs) that may have a group or pool of technicians that may need to access a customers environment to perform an operation, whether this is planned work or reactive support to an ongoing issue.
Use Case 2 – Helpdesk Operations/User Onboarding
While we would suggest to never log on as another user, there are times when troubleshooting issues that you need to be able to be logged in as the user. For this, some organizations will enable shared user support for the end-user object so that technicians can log in as the user, when required. Again, it is not a best practice to log in as another user, but with Secret Double Octopus we have a full audit trail of who is logging into machines as various user objects.
Logging into a machine as an end user, especially when the user is being onboarded to the organization, is helpful. This allows the IT staff to ensure the machine is setup, configured and ready for the end user when they start.
Use Case 3 – Application Requirements
Some applications must be run as a specific user, with SDO, you can easily log onto the machine as the shared user to ensure the application is run as the required shared user. This is most common in manufacturing environments where you have multiple shifts using the same machine and the machines cannot be logged out due to processes going on for the manufacturing process. We also see this in healthcare organizations that have process flows where multiple different users will log onto a machine during the course of a patient visit.
Shared User Account Experience
Ok, now we know typical use cases for shared users, but what does that look like? Is it easy? Is it annoying? Let’s take a look at the end-user experience for a Windows login as well as launching an application as a different user.
The Windows login experience is almost identical to what we showed in our previous blog post focused on the standard user login experience. There is one key difference with this experience, we will click a small link at the login screen to activate the shared user option. Let’s start with a quick video of the shared user experience for Windows login. The below video will show the following steps in the overall process
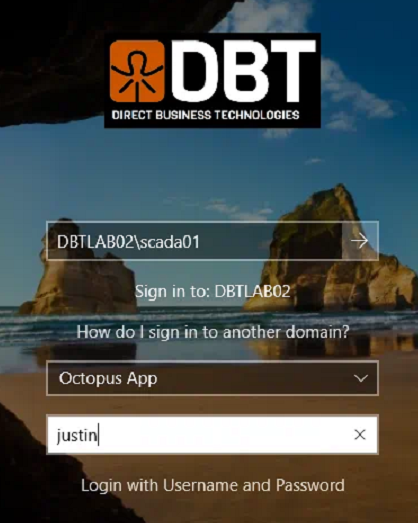
- 1. In the top username field, enter the shared username you are needing to log onto the Windows computer as (scada01 in the video below)
- 2. Select your authenticator (if applicable)
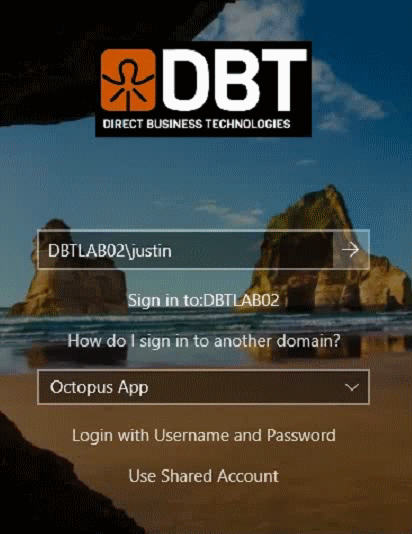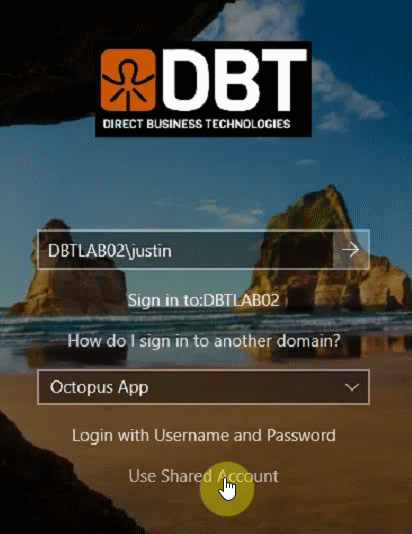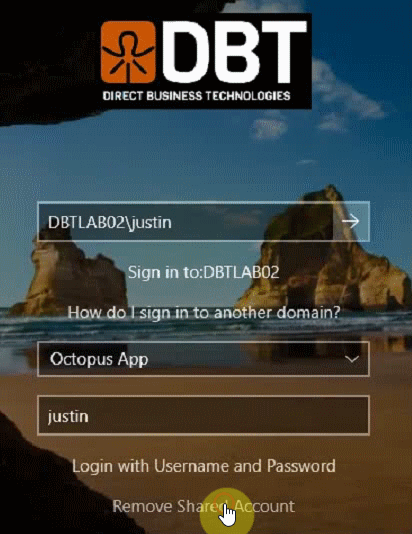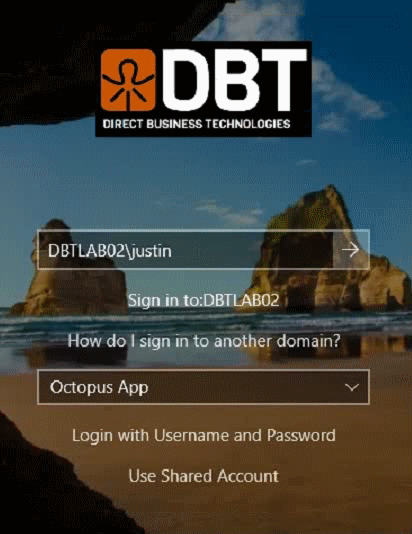
- 3. Click on the Use Shared Account link at the bottom
- 4. Enter in the username you want to use for authentication, this is the user that will receive the push notification for authentication (user justin in the video below)
- 5. Approve push notification
- 6. Supply your biometric, faceID, or phone passcode to your mobile device
- 7. Get signed in
- 8. Review of audit logs that show that user justin authenticated as shared user scada01
Setup and Configuration
To setup and configure shared user accounts within the Secret Double Octopus platform we must configure the shared user objects within the management console interface and we must enable the shared user feature within the Octopus Desk package/settings. Each of these tasks is broken down below.
Management Console Configuration
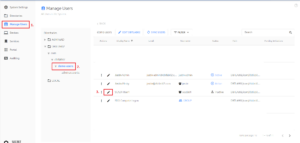
Once you are logged into the Secret Double Octopus management console:
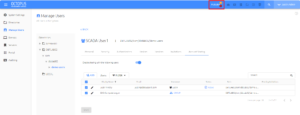
- 1. click on Manage Users in the left-hand navigation menu
- 2. Browse to the user object in your directory. You can also use the search box on the right-hand side of the screen to find the user object
- 3. Click on the pencil icon to edit the user you want to make a shared user
Inside of the user object properties, do the following:
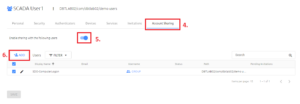
- 4. click on Account Sharing in the center menu options tabs
- 5. Turn on the Enable sharing with the following users option (The toggle should be blue)
- 6. Click on the Add button to add users or groups that are allowed to authenticate as the this shared user
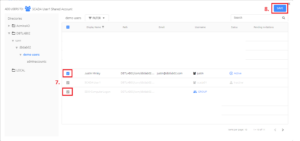
In the ADD USERS TO: window that opens, select the users and/or groups you want to be able to log in as the shared user object. In this example, SDO-ComputerLogon was already selected, so it is greyed out. We are adding Justin Mirsky (Hey, that’s me!) to the defined list:
- 7. click on Account Sharing in the center menu options tabs
- 8. Turn on the Enable sharing with the following users option (The toggle should be blue)
9. Final step in the management console! Up to now, you have made configuration changes and these have been stored in the backend configuration database. To make the changes live/active, you have to publish the change to the authentication servers. If you are familiar with Cisco networking, think of this as a “copy start run” command or a commit operation on a Palo Alto firewall. This publish operation takes the changes and pushes them down to a high-performance Redis cache running on each authentication server role. After clicking publish, you will be prompted again to confirm the publish operation, that second screenshot is not shown below.
Octopus Desk Configuration
Now that we have the backend configuration completed, we need to build the installation package for Secret Double Octopus to include support for the shared users. If you have an existing deployment of the Octopus Desk client (Version 3.9.0 or higher), these adjustments can be made with registry key changes if you do not want to build a new installation package and push it out. I will highlight those registry keys a bit further down. Configuration of the Octopus Desk client will be a blog post all on its own, I will update this post in the future to link this section to the blog post on the Octopus Desk build process when that content is ready.
The Octopus Desk package is customized via a tool called the Octopus Desk MSI Updater and is provided by Secret Double Octopus. This tool allows you to adjust all supported parameters of the deployment package to meet your needs. There are a significant number of options, we will be focused on just three options today; Shared Account Support, Allow Switching Between Shared and Regular Accounts, and Use Regular Account as Default with Shared Account Enabled.
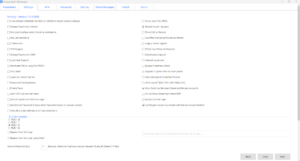
Let’s break down each of these options.
••Shared Account Support
This is required at all times if you want to use shared accounts / shared users. This is the base option to turn on support for this in the Octopus Desk package. This checkbox determines the setting of a registry key on the system. The corresponding registry key for this is located at [HKEY_LOCAL_MACHINE\SOFTWARE\SecretDoubleOctopus\WCPS]:
REG_DWORD – Shared Account Support
Value – 0 = Off/Disabled, 1=On/Enabled
![]()
Having only this option enabled, results in the following user experience. Notice that the second username field is present at all times, there is no link to switch between standard and shared users.
- •Allow Switching Between Shared and Regular Accounts
When off (not checked), SDO will only allow shared user objects to log onto a machine. When on (checked), SDO will allow you to switch between a standard account and a shared account. Note, during the demo video at the beginning of this blog post, I had this option turned on, which is why there was a link called Use Shared Account that I had to click to log in as the shared account. The corresponding registry key for this is located at [HKEY_LOCAL_MACHINE\SOFTWARE\SecretDoubleOctopus\WCPS]:
REG_DWORD – Show Shared Account Link
Value – 0 = Off/Disabled, 1=On/Enabled
Having this option enabled results in the following user experience. Note in animation below we are switching between standard user and shared account login
- •Use Regular Account as Default with Shared Account Enabled
This does exactly what it sounds like. It will default to using a standard user account and allow you to click the Use Shared Account link to activate the shared user feature. This is particularly useful for organizations that want to deploy a single installation package, but need both options available. This, in my opinion, should be the default setting for shared accounts
Embracing the Future with Passwordless Security
I hope you enjoyed this post and found it useful. Feel free to CONTACT US if you have questions or would like to get a more in-depth demo of the Secret Double Octopus platform. This feature and the SDO platform as a whole are an easy way for organizations to adhere to compliance requirements, secure their systems and improve their end user experience.
In our World, where security breaches and identity theft are increasingly common, the need for robust security measures has never been more pressing. Secret Double Octopus not only enhances security by eliminating traditional passwords but also simplifies the user experience, making it both secure and user-friendly. By integrating passwordless authentication for shared user accounts, organizations can ensure a higher level of compliance and accountability.
As we have explored, the flexibility of Secret Double Octopus allows for a tailored approach, ensuring that even shared accounts—often necessary but vulnerable—are protected under stringent security protocols without sacrificing convenience. This dual benefit of enhanced security coupled with ease of use represents a significant step forward in managing user identities in complex environments like Active Directory.
Looking ahead, the continuous improvements in authentication technologies promise even more secure and seamless access management solutions. Organizations adopting these innovations, such as the capabilities provided by Secret Double Octopus, position themselves at the forefront of cybersecurity, ready to face the challenges of tomorrow’s IT landscapes.