
INTERNAL
PEN TESTING
Assessing Your Network’s Vulnerabilities from the Inside
Our internal penetration testing service, powered by the Horizon3.ai NodeZero™ platform, is designed to emulate the actions of an attacker or a malicious insider with existing access to your network. By simulating both network-only and credentialed user access, we can identify potential actions that various user roles could execute in the event of a ransomware strike or a phishing breach. We scrutinize multiple facets of your infrastructure, including:
- On-Premises Systems: Assessing the security of physical hardware and network resources within your organization.
- Cloud Environments: Evaluating the defenses of your cloud-based resources and services.
- Identity and Access Management: Testing the resilience of systems managing user identities and permissions.
- Data Systems: Inspecting the protection around your stored and in-transit data.
- Virtualized Resources: Analyzing the robustness of your virtual servers and services.
Automated Discovery and Exploitation:
NodeZero™ is adept at autonomously pinpointing and exploiting network vulnerabilities, mimicking the approach of real-world cyber adversaries. The platform adeptly navigates through your network environment, executing tasks such as:
- Credential Compromise: Executing credential attacks to capture user access details.
- Data Mining: Locating and leveraging exposed data within the network.
- Control Circumvention: Bypassing implemented security measures.
- Exploit Execution: Targeting critical vulnerabilities and misconfigurations for lateral movements.
Illustrating the Real Risks: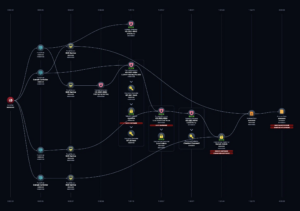
NodeZero™ leverages a comprehensive suite of offensive security tools, chaining together vulnerabilities to reveal the potential consequences of an attack, including:
- Domain Takeover: Demonstrating the ramifications of compromised administrative credentials.
- Email System Breach: Illustrating risks associated with business email compromise.
- Sensitive Data Access: Exposing potential data leakage points.
- Ransomware Susceptibility: Highlighting areas vulnerable to encryption-based attacks.
- Cloud Infiltration: Assessing the ability of an attacker to extend their reach to cloud assets.
- And many other potential threats.
By presenting real-world attack scenarios, such as a ransomware pathway where NodeZero™ first seizes a domain admin account and then accesses critical data, we provide a vivid demonstration of potential organizational risks and offer tailored recommendations for bolstering your defenses.
Diverse Perspectives in Internal Penetration Testing
Multi-Angled Assessments with NodeZeroTM
Our internal penetration tests via NodeZeroTM offer a comprehensive security evaluation by simulating various threat perspectives. This multifaceted approach allows you to “threat model” your network effectively. NodeZeroTM can assess the resilience of each network segment—be it the server subnet, user subnet, or the DMZ (demilitarized zone)—as well as your data centers. Simulate the consequences of compromised credentials with scenarios like a phishing attack on your HR department or a rogue IT staff member. Alternatively, engage in a “black box” penetration test, where NodeZeroTM begins with zero credentials and must find its own way into the system.
Extensive and Simultaneous Testing Capabilities NodeZeroTM transcends the limitations of manual penetration tests, which typically cover less than one percent of a network. It is designed to accommodate even the most extensive networks, allowing you to specify IP ranges for inclusion or exclusion. You have the option to test the entirety of your private IP space, as defined by RFC 1918. Furthermore, you can initiate multiple concurrent tests across various network segments to maximize efficiency and coverage.
Internal Penetration Test Features
Comprehensive Asset Discovery and Network Enumeration
In its initial phase, NodeZeroTM identifies and catalogs a wide array of network assets, from hosts and devices to cloud services and applications. It discerns routers, domain controllers, VMware vCenter servers, databases, and more, detecting open TCP and UDP ports along with the services they host. The platform meticulously determines operating systems, web servers, and applications, providing a detailed network blueprint.
Surpassing CVEs with Advanced Detection
 NodeZeroTM delves deeper than standard vulnerability scanners, which primarily target common vulnerabilities and exposures (CVEs). It autonomously uncovers and exploits critical weaknesses, executing attack paths that reflect actual exploitable vulnerabilities within your network. These paths often don’t rely on exploiting known CVEs but instead utilize a chain of weaknesses that mimic the strategies of real-world attackers.
NodeZeroTM delves deeper than standard vulnerability scanners, which primarily target common vulnerabilities and exposures (CVEs). It autonomously uncovers and exploits critical weaknesses, executing attack paths that reflect actual exploitable vulnerabilities within your network. These paths often don’t rely on exploiting known CVEs but instead utilize a chain of weaknesses that mimic the strategies of real-world attackers.
The results and impact scores provided post-testing are based on NodeZero’s achievements during the test—offering a dynamic evaluation compared to static CVE scores that may not reflect the true exploitable threat within your unique environment.
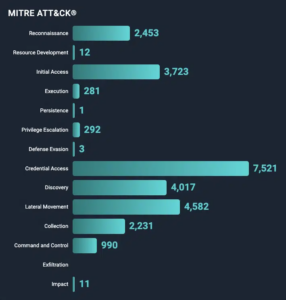
NodeZeroTM aligns its attack modules with the MITRE ATT&CK framework, providing you with detailed insights into the tactics, techniques, and sub-techniques used during the penetration test. This offers you a strategic understanding of how potential attackers could navigate your network and the steps you can take to strengthen your defenses.